18+ initialization vector attack
Boot or Logon Initialization Scripts Logon Script Windows Login Hook. The protocol is composed of two layers.

Initialization Vector Attacks Comptia Security Sy0 301 3 4 Youtube
The same is true for.

. This address is always located in the BIOSUEFI flash memory on the motherboard. More information about the DLL Preloading remote attack vector. 05 Dec 17.
The below data illustrates why zero initializing is better for code size. Historically known as the old ARPANET routing algorithm or known as Bellman-Ford algorithm. RFC 8446 TLS August 2018 receiver.
A Man-in-the-Middle MitM attack D. In x86x64 this address is 4GB minus 16-bytes FFFF_FFF0h. The usual methods for generating IVs are predictable sequences of numbers based on for example time stamp or sector number and permit certain attacks such as a watermarking attack.
Inter-process Communication using a shared stack. 1820 rounds are suggested as sufficient protection. For example the injected code could hook system function calls or read.
12Major Differences from TLS 12 The following is a list of the major functional differences between TLS 12 and TLS 13. Start of execution in the CPU processor reset vector. Initializing using general-purpose registers.
An endpoint that is transmitting records. AutoPlay is based on a set of handler applications registered with the. Evaluate the following to identify the statements that are true about nonces IVs and saltsSelect two A.
One way to strengthen a key is to add a nonce or an Initialization Vector IV. Get first and last elements from Array and Vector in CPP. It is not intended to be exhaustive and there are many minor.
The biases and weights in the Network object are all initialized randomly using the Numpy nprandomrandn function to generate Gaussian distributions with mean 0 and standard deviation 1. Each file uses a single data key to encrypt all values of a document but each value receives a unique initialization vector and has unique authentication data. An initialization vector IV or starting variable SV is a block of bits that is used by several modes to randomize the encryption and hence to produce distinct ciphertexts even if the same plaintext is encrypted multiple times without the need for a slower re-keying process.
National Institute of Standards and Technology NIST in 2001. Similarities and Differences between Ruby and C language. Encrypted salt-sector initialization vector ESSIV ESSIV is a method for generating initialization vectors for block encryption to use in disk encryption.
ˈrɛindaːl is a specification for the encryption of electronic data established by the US. The same is true for passwords which can be strengthened by adding a salt to a hashed password value. Path traversal vulnerability where an attacker can target the preview FilePath parameter of the getPreviewImage function to get access to arbitrary system file.
Citation neededAn initialization vector has different security requirements than a key so the IV usually. Drupal core Un-restricted Upload of File. The term BIOS Basic InputOutput System was created by Gary Kildall and first appeared in the CPM operating system in 1975 describing the machine-specific part of CPM loaded during boot time that interfaces directly with the hardware.
Retrieved December 5 2014. At the lowest level layered on top of some reliable transport protocol eg TCP is the TLS Record Protocol. AES is a variant of the Rijndael block cipher developed by two Belgian cryptographers Joan Daemen and Vincent.
The Advanced Encryption Standard AES also known by its original name Rijndael Dutch pronunciation. This random initialization gives our stochastic gradient descent algorithm a place to start from. Check for integer overflow on multiplication.
One way to strengthen a key is to add a nonce or an Initialization Vector IV. Control-Alt-Delete often abbreviated to CtrlAltDel also known as the three-finger salute or Security Keys is a computer keyboard command on IBM PC compatible computers invoked by pressing the Delete key while holding the Control and Alt keys. CtrlAltDeleteThe function of the key combination differs depending on the context but it generally interrupts or facilitates.
Our peers at Google have done some measurements and proven that on Clang zero initialization is currently measurably better in code size and runtime performance than pattern initialization. The endpoint that did not initiate the TLS connection. AutoPlay is a feature introduced in Windows XP which examines removable media and devices and based on content such as pictures music or video files launches an appropriate application to play or display the content.
Brazilian banking malware goes global. In later chapters well find better ways of initializing the weights and biases but. In computer programming DLL injection is a technique used for running code within the address space of another process by forcing it to load a dynamic-link library.
Every time sops encounters a leaf value a value that does not have children it encrypts the value with AES256_GCM using the data key and a 256 bit random initialization vector. A CPM machine usually has only a simple boot loader in its ROM. Apply updates per vendor instructions.
Key strength is based on length and randomness. LazyScripter has used spam emails weaponized with archive or document files as its initial infection vector. If available settings in an autoruninf file can add to the options presented to the user.
Lokibot is delivered via a malicious XLS attachment contained within a spearhpishing email. The TLS Record Protocol and the TLS Handshake Protocol. Bellman Ford Basics Each router maintains a Distance Vector table containing the distance between itself and ALL possible destination nodes.
An impersonation attack C. In all platforms the bootstrap processor BSP starts execution by fetching the instruction located in an address known as the reset vector. Buffer Overflow Attack with Example.
Versions of MS-DOS PC DOS or DR-DOS contain a file called variously. An endpoint that is receiving records.
With our money back guarantee our customers have the right to request and get a refund at any stage of their order in case something goes wrong. 50 Network Troubleshooting and Tools. The SSL protocol as used in certain configurations in Microsoft Windows and Microsoft Internet Explorer Mozilla Firefox Google Chrome Opera and other products encrypts data by using CBC mode with chained initialization vectors which allows man-in-the-middle attackers to obtain plaintext HTTP headers via a blockwise chosen-boundary attack.
Browse our listings to find jobs in Germany for expats including jobs for English speakers or those in your native language. 15 Jan 19. Leviathan has sent spearphishing emails with malicious attachments including rtf doc and xls files.
Retrieved January 18 2022. A distance-vector routing DVR protocol requires that a router inform its neighbors of topology changes periodically. A Denial of Service DoS attack B.
DLL injection is often used by external programs to influence the behavior of another program in a way its authors did not anticipate or intend. RFC 5246 TLS August 2008 1Introduction The primary goal of the TLS protocol is to provide privacy and data integrity between two communicating applications.

Python Pycrypto How Does The Initialization Vector Work Stack Overflow
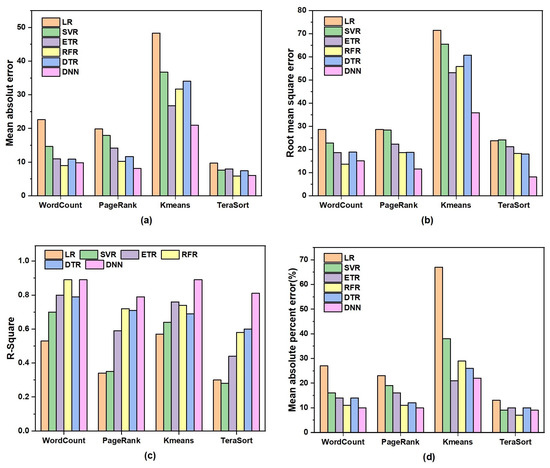
Sensors August 1 2022 Browse Articles
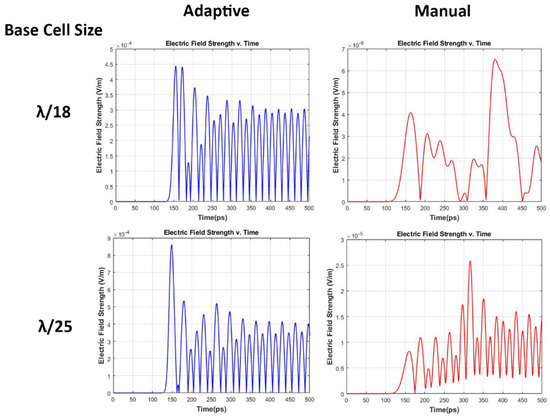
Sensors August 1 2022 Browse Articles
What Is The Meaning Of Initialization Vector Technology Innovation Internet And Security Science

Security And Privacy In Unified Communication Acm Computing Surveys
Benchmarking The Performance Impact Of Linux 5 15 S Newest Protection Around Side Channel Attacks Phoronix

Initialization Vector Attacks Comptia Security Sy0 301 3 4 Youtube
Taxonomy Of Attack Vector Types In Mobile Computing Download Scientific Diagram

Initialization Vector Attacks Comptia Security Sy0 301 3 4 Youtube

Initialization Vector Attacks Comptia Security Sy0 301 3 4 Youtube

Security And Privacy In Unified Communication Acm Computing Surveys

Owasp Top Ten Proactive Defenses Ppt Download
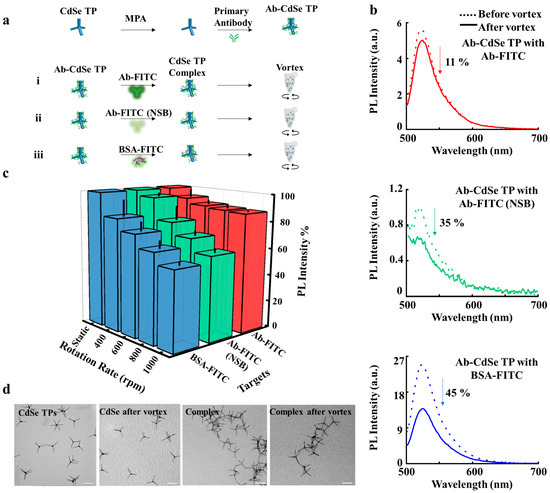
Sensors August 1 2022 Browse Articles

Protocol Design How Are Initialization Vectors Used In Tls 1 1 Cryptography Stack Exchange

Security Why Is Using A Non Random Iv With Cbc Mode A Vulnerability Stack Overflow

What Is Initialization Vector
Cissp Video Course Video